Open Food Facts Data Analysis
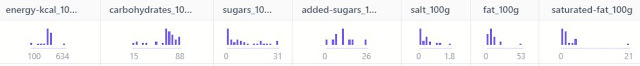
As a self-taught nutrition enthusiast , I have been contributing to the crowdsourced India database of Open Food Facts - "the Wikipedia of food", by adding and editing products. The decentralized open source project has data on more than 3 million products (as of April 2024) from countries around the world. Open Food Facts (OFF) data is released as Open Data: it can be reused freely by anyone, under the Open Database License (ODBL). I've been cleaning up & compiling the data by food categories to extract insights . There are multiple ways to get the data : CSV or Excel format using the advanced search feature MongoDB daily export - more than 30GB uncompressed! JSONL daily export CSV daily export API As I was interested in select product features and macronutrient details, I decided to use the OFF API. This is how the process for compiling data for each food category currently goes: 1. I construct the following URL with the fields I require to fetch the nutrition dat
