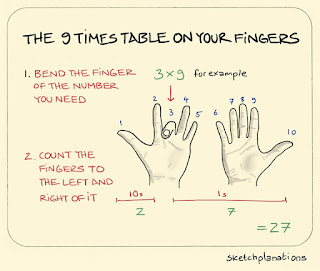
Annotated comparison table derived from official Azure documentation - Ultra disk Premium SSD Standard SSD Standard HDD Disk type SSD SSD SSD HDD Scenario IO-intensive workloads such as SAP HANA, top tier databases (for example, SQL, Oracle), and other transaction-heavy workloads. Production and performance sensitive workloads Web servers, lightly used enterprise applications and dev/test Backup, non-critical, infrequent access Max disk size 65,536 gibibyte (GiB) Range - Fixed sizes from 4 GiB up to 64 TiB 32,767 GiB 32,767 GiB 32,767 GiB Max throughput 2,000 MiB/s Range - 256 KiB/s for each provisioned IOPS to 2000 MBps per disk 900 MiB/s 750 MiB/s 500 MiB/s Max IOPS 160,000 Range - 300 IOPS/GiB to 160 K IOPS per disk 20,000 6,000 2,000 Notes Outbound data transfers (data going out of Azure data centers) incur billing for bandwidth usage Some of the current limitations: - Supported only in regions - Can only be used with avail